risk assessment

Introduction to Risk Analysis
Security in any system should be commensurate with its risks. However, the process to determine which security controls are appropriate and cost effective is quite often a complex and sometimes a subjective matter. One of the prime functions of security risk analysis is to put this process onto a more objective basis.
There are a number of distinct approaches to risk analysis. However, these essentially break down into two types: quantitative and qualitative.
Quantitative Risk AnalysisThis approach employs two fundamental elements; the probability of an event occurring and the likely loss should it occur.
Quantitative risk analysis makes use of a single figure produced from these elements. This is called the 'Annual Loss Expectancy (ALE)' or the 'Estimated Annual Cost (EAC)'. This is calculated for an event by simply multiplying the potential loss by the probability.
It is thus theoretically possible to rank events in order of risk (ALE) and to make decisions based upon this.
The problems with this type of risk analysis are usually associated with the unreliability and inaccuracy of the data. Probability can rarely be precise and can, in some cases, promote complacency. In addition, controls and countermeasures often tackle a number of potential events and the events themselves are frequently interrelated.
Notwithstanding the drawbacks, a number of organizations have successfully adopted quantitative risk analysis.
Quantitative Risk Analysis
This is by far the most widely used approach to risk analysis. Probability data is not required and only estimated potential loss is used.
Most qualitative risk analysis methodologies make use of a number of interrelated elements:
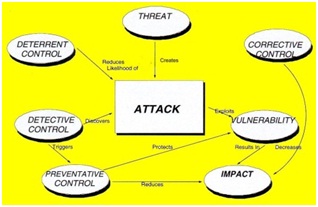
THREATSThese are things that can go wrong or that can 'attack' the system. Examples might include fire or fraud. Threats are ever present for every system.
VULNERABILITIESThese make a system more prone to attack by a threat or make an attack more likely to have some success or impact. For example, for fire vulnerability would be the presence of inflammable materials (e.g. paper).
CONTROLSThese are the countermeasures for vulnerabilities. There are four types:
• Deterrent controls reduce the likelihood of a deliberate attack
• Preventative controls protect vulnerabilities and make an attack unsuccessful or reduce its impact
• Corrective controls reduce the effect of an attack
• Detective controls discover attacks and trigger preventative or corrective controls.
These elements can be illustrated by a simple relational model: